Using kali linux for Advanced Security Testing - Alphaomikron
Written by BLOGDAY Updated at Mar 07, 2024 | Reading time: 4
Strong security measures are essential in the current digital environment, where cyber dangers are pervasive. The book "Advanced Security Testing with Kali Linux" shines as a knowledge-filled guide that leads readers through the complex world of cybersecurity. With the help of the potent tools provided by Kali Linux, this book aims to provide security enthusiasts and experts with the knowledge and abilities needed to successfully traverse the challenging field of security testing.
Chapter 1: Conditions of Use and Disclaimer
It is important that we have a clear grasp of the terms of participation before we set out on our adventure. The ethical issues and legal restrictions that control security testing operations are described in this chapter. It is recommended that readers follow moral guidelines and legal requirements in order to guarantee that they act responsibly and legally when conducting security tests.
Chapter 2: Configuring and Installing Virtual Machines
It's crucial to lay a strong foundation before tackling the complexities of security testing. This chapter explains how to use VMware Player to set up a virtual lab environment. Readers can safely and effectively experiment with security testing approaches by simulating real-world circumstances in a controlled environment through the creation of virtual machines (VMs) and configuration of network settings.
Installing Kali Linux in Chapter Three
With its abundance of tools and utilities designed specifically for security testing, Kali Linux is a mainstay in the toolbox of security experts. Readers will discover how to set up Kali Linux for best performance and compatibility with their virtual lab environment in this chapter. A seamless installation procedure is facilitated by the provision of step-by-step instructions and troubleshooting advice.
Chapter 4: Kali Linux Update
The field of cybersecurity is always changing as new exploits and vulnerabilities appear on a regular basis. It's essential to maintain Kali Linux updated with the newest security patches and software updates in order to stay ahead of any attacks. This chapter explains how to update Kali Linux so that readers can benefit from the newest features and tools available to support their security testing efforts.
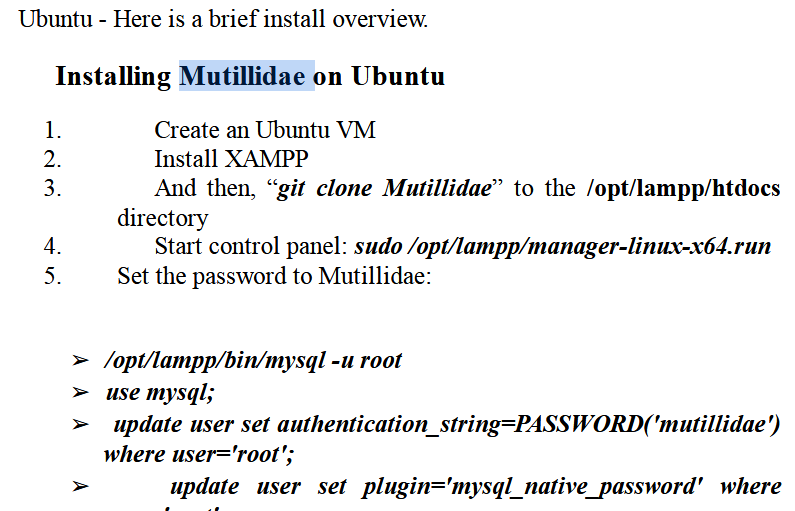
Chapter 5: Examining the Mutillidae Family and Beyond
Mutillidae is a web application that is full with flaws that can be exploited, making it the ideal environment for sharpening security testing skills. Readers will explore popular web application vulnerabilities including SQL injection, cross-site scripting (XSS), and command injection as they dig into the complexities of Mutillidae in this chapter. Readers are given the tools to put their newly acquired knowledge to use in locating and fixing security vulnerabilities in web applications through practical examples and hands-on activities.
Chapter 6: Advanced Methods for Penetration Testing
The foundation of security testing methodology is penetration testing, which enables organizations to proactively detect and fix security flaws before malevolent actors take advantage of them. Advanced penetration testing methods, such as network reconnaissance, exploitation, privilege escalation, and post-exploitation tasks, are covered in detail in this chapter. Readers will discover the ins and outs of penetration testing and how to strengthen and evaluate target systems' security posture through case studies and real-world examples.
Chapter 7: Evaluation and Handling of Vulnerabilities
In order to protect against possible security threats, effective vulnerability assessment is essential. It gives businesses important insights into how easily their IT infrastructure might be exploited. The foundations of vulnerability assessment are covered in this chapter, including initial identification, prioritizing, remediation, and risk reduction. By using both automatic scanning tools and manual procedures, readers will gain knowledge on how to find vulnerabilities and fix them, strengthening their systems' defenses against cyberattacks.
Securing Network Infrastructure in Chapter 8
Any strong cybersecurity strategy must start with network security, which includes a wide range of methods and best practices to prevent unwanted access and data breaches. This chapter explores the complexities of protecting network infrastructure, including secure network protocols, virtual private networks (VPNs), intrusion detection and prevention systems (IDPS), and firewall setup. Readers are equipped with useful advice and real-world examples to put strong network security measures in place and guard against a variety of cyberthreats.
Chapter 9: Beyond Ethical Hacking
A powerful tool in the battle against cybercrime is ethical hacking, which enables security experts to think like hostile adversaries in order to spot and address any security flaws. The process of ethical hacking is covered in this chapter, from information collecting and reconnaissance to vulnerability research and exploitation. Through the adoption of ethical hacking approaches and the utilization of Kali Linux tools, readers will acquire the necessary skills and experience to carry out thorough security audits and enhance the resilience of the digital assets inside their businesses.
In conclusion, "Advanced Security Testing with Kali Linux" is an all-inclusive manual for experts and security enthusiasts who want to improve their cybersecurity skills. With the help of useful tutorials, real-world case studies, and practical exercises, readers may acquire the information and abilities needed to successfully traverse the challenging field of security testing. Readers may strengthen their businesses' defenses against developing cyber attacks and protect against potential security vulnerabilities by utilizing the potent tools and utilities provided by Kali Linux. This book is an essential tool for everyone who is dedicated to maintaining the integrity of global digital ecosystems and cybersecurity principles as the digital landscape changes.
THE LINK IS HERE :
CLICK HERE
Search
Categories
Latest posts
كورس صناعة الفيديو والكولاج في الافترافكت كورس احترافي
Nov 14, 2024 | Arabic blog
6 Weeks Bootcamp for Civil & Construction Engineer from Zero
Nov 14, 2024 | Business & Entrepreneurship
Cyber Security: Anti-Virus
Nov 12, 2024 | Cybersecurity
Simple React App from Scratch
Nov 12, 2024 | Web Development
دليل التسويق بالعمولة النهائي لإتقان الربح [عربي]
Nov 10, 2024 | Arabic blog